
4 min read
Meeting the New, AI-Enabled Face of Risk
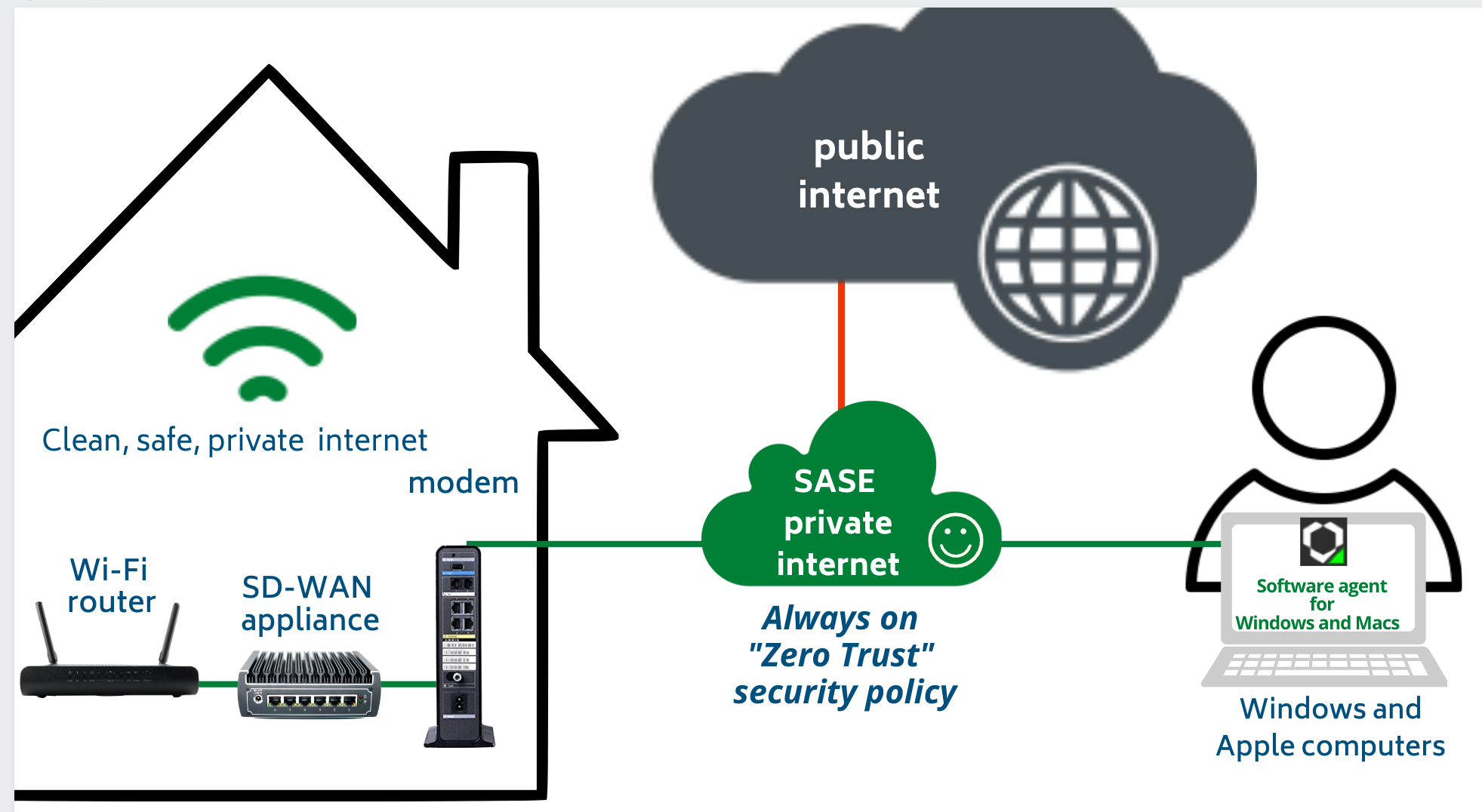
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network security technology. Purpose-built for the most sensitive, mission-critical environments, it delivered the...
Read More




























.png?width=2000&height=1047&name=TDS%20Red%20Five%20(2).png)



