5 min read
Meeting the New, AI-Enabled Face of Risk
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

Email is where over 85% of all cyber-related damages start. Over 90% of malware is delivered via email. In 2020, malware attacks increased by 358%. The inbox has become the frontline in the war against losses from cybercrime and online fraud. In 2021, AI has come into play, and it will eventually change the way we think about personal email forever.
Most cyber damages start at one of three places called "The Three Primary Attack Surfaces" defined here. Email is defined as "Attack Surface #1."
Most email attacks are a version of phishing and spoofing. The earliest email phishing exploits were obvious with misspellings, bad grammar, and an unbelievable premise – like informing you of winning the Nigerian lottery. Phishing has evolved with more convincing content, good logos and graphics, and more reasonable requests. Even so, a phishing email of this version is easy to spot with a glance at the sender’s email address.
Image: Phishing email purportedly from Chase Bank is easy to spot by revealing the sender’s address and lack of chase.com as the email domain.
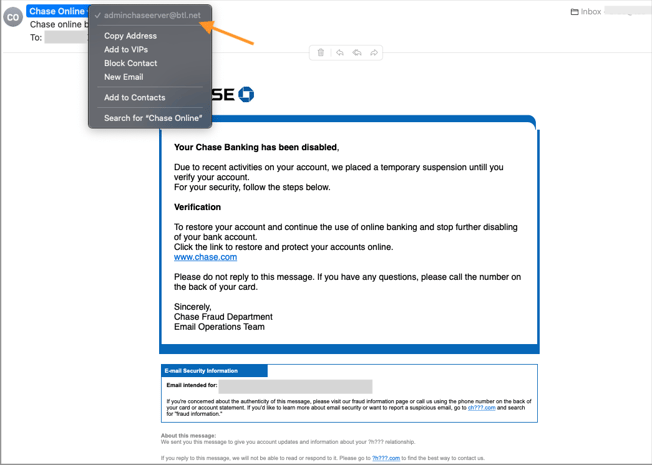
More recently, phishing has evolved to “spoofing.” Here, the sender seems genuine even when inspecting their email address and sending domain. For example, in the image of the phishing email above, clicking to see the sender’s full email address will reveal a chase.com domain. This variant is known as domain spoofing, and it is shockingly easy for anyone to do. In domain spoofing, only advanced authentication measures can screen the email spoof from getting to the inbox.
A good spoofing email can be tough to discern for an average user because from everything they can see and check, what they are looking at is credible and seems legitimate. The email spoof will use social engineering techniques to prompt a simple action, like a mouse click, which can launch a malware attack such as ransomware, spyware, and command-and-control of the computer.
The next generation of email exploits is emerging and using AI software to advance attacks. With massive amounts of stolen personal information and seemingly infinite datasets from which to draw upon, AI software creates a persistent system of feedback loops that continually optimize the attacks for efficacy and success.
In this approach, hackers target each inbox with a bespoke attack using sophisticated detail and engineering. Additionally, because AI “thinks” differently than humans, exploits and strategies out of the grasp of our imagination will present themselves, and the system will begin tactical planning for the following variant of attack.
Criminal syndicates have prepared for the profits they see ahead with AI-enhanced exploits. They’re leveraging up by building “cybercrime-as-a-service” platforms for recruiting affiliates (i.e., anyone who can use a keyboard) to distribute their malware-infected email and split the spoils. Cybercrime-as-a-service coupled with AI, and infinite amounts of stolen personal data present an enormously scalable operating model. Massive profits and digital currencies in cybercrime will drive email-related losses to unprecedented levels, and no inbox will go unaffected.
“When AIs start hacking, everything will change. They won’t be constrained in the same ways, or have the same limits, as people. They’ll change hacking’s speed, scale, and scope, at rates and magnitudes we’re not ready for."
Bruce Schneier
April 26th, 2021
from Dr. Schneier’s 16th book on cybersecurity:
"When AIs Start Hacking"
Most personal email account holders are unprepared for the onslaught their inbox will face. They’re using “free” email from providers like Yahoo, AOL, Gmail, MSN, and others, including the Baby Bell and cable providers. These email systems are built primarily for scale and information mining, not information security. For example, Google just disclosed Gmail monitors and collects personal information including:
By any standard, this level of information collection qualifies as surveillance and is unsuitable for private clients and high-profile individuals.
✓ For privacy, security, and digital autonomy, it’s time to reconsider your personal email account.
The worst thing that can happen to your email account is an account-level hack. Here, the hacker is inside the email account and has complete administrative control. They skulk and collect personal data to inform and optimize the attack. When a skillful hacker uses advanced systems to plot strategy, the victim is clueless and at the whim of the bad actor, typically unknowing until well after the perpetrator is gone.
There are three components to securing your email account – each as critical as the other.
It’s unavoidable and using art and science in password management is essential today. The rules are passwords must be long, 14 characters minimum, and unpredictable. Using a password manager makes things much more secure and convenient, and knowing some tricks helps a lot. Using a random phrase that creates mental imagery helps to recall the password. For example, the password Cowboy-palm-tree-moon* creates an indelible image in the mind’s eye, yet is an excellent password because it is long, 22 characters, and not a predictable phrase, like Mary-had-a-little-lamb*.

Enabling multi-factor authentication (“MFA”) in your email account almost eliminates the risk of an account-level hack. Microsoft says 99.99% of account-level email hacks could be avoided by using MFA.
Using SMS text for MFA codes is reasonably safe for most of us, but others opt to use a password authenticator to eliminate the risk of their mobile accounts being hacked and used for message spoofing.
Cybercriminals target people more than technology – they’re easier to hack.
Learn to think critically in the inspection of email and follow these two best practices:
Privatizing email means owning a web domain for personal email. Registration and private listing fees are modest and accessible to anyone. It’s essential to choose a good host from which email boxes and folders are kept on secure servers and are safely accessible from the cloud. Quality hosting providers include enhanced enterprise-grade security features and authentication measures. Email is built for security and user experience in this approach, not for ads and information mining.
Email security is big business and rich with innovation. With a private email domain and a professional provider, email security is built-in and is a critical part of their value proposition. New features are added as the market evolves, unlike the “free” provider who sees the inbox differently – as a product to sell to a third party – a source for their profits.
Progress in AI is enhancing cybersecurity too, and much of the innovation is related to protecting the inbox. Professional email domain hosting providers incorporate new features as the industry advances to counter the threat. Inbound emails are screened, filtered, credentialed, authenticated, and sand-boxed using advanced software and threat intelligence. While we cannot eliminate cyber risk, the layered measures are effective and significantly mitigate the potential for loss.
For the private client, one-time and recurring costs associated with a private email domain are affordable and represent value in the form of enhanced privacy, security, and self-ownership of personal information.
Self-ownership of personal information will be increasingly critical for privacy, security, and personal safety. Private parties must begin to shore in their personal data; privatizing email takes a meaningful step in the right direction. With a private email domain, the information, content, attachments, logs – all of it is yours and includes the beneficial rights of ownership enjoyed with any asset.
For more information about private email and cybersecurity products:

5 min read
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

9 min read
Over the past decade writing these letters, I’ve made it my mission to help you navigate the digital age with confidence and resilience. If I have...

4 min read
For generations, family offices and ultra-high net worth families have mastered the art of estate planning — preserving wealth, ensuring succession,...