5 min read
Meeting the New, AI-Enabled Face of Risk
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

This month's CyberAdvisor covers these four main topics:
It's been known for a long time - Big Tech is an abuser of enormous power and influence, an exploiter of privacy and personal information, and consistently clever in their dishonesty with the rest of society. And exhibit "A" for Big Tech's misbehavior has always been Google.
But earlier this year, Apple's new privacy policies forced Google's hand to reveal the extent of their data collection. Now we see how truly awful the worst of the worst is.
You can click here to see facts about the extent of Google's data collection practices. Still, in a nutshell, you'll find it's pretty much everything - including information unrelated to their products and information about your contacts.
If you use their products, Google knows:
In addition, they know where you are, where you’ve been, and where you will likely go next. Google also controls all your ‘content’ – pictures, videos, audio files, and documents. And, if they don’t like your content, they can unilaterally lock you out.
These data collection practices store enormous volumes of data subjected to algorithms and AI software for analysis and engineering. With goals of maximizing their power and profits, Google, in turn, shows you the internet they want you to see. All this, conducted by unaccountable parties holding your data for an indefinite time. Such is your contractual agreement using Google's products.
Google even scans the emails of non-subscribers who send emails to Gmail accounts. These are people that have not signed up for Gmail, yet their information is collected, stored, analyzed, and sold by Google.
“Google doesn’t care about protecting user privacy, they care about protecting their surveillance business model. If they really cared about privacy, they would just stop spying on billions of people around the world.”
DuckDuckGo earlier this year when Google finally revealed their data collection practices.
✓ Google is a massive commercial surveillance system without accountability and with a consistent record of overreach and deception.
Anyone concerned with privacy and personal security and desires some level of individual autonomy must recognize the stakes with Big Tech. Fortunately, individuals have choices and can take alternative actions that de-centralize from Big Tech's grasp and takes back a meaningful chunk of your digital life.
The obvious place to start with de-centralizing from Big Tech is with Google. And the most effective first step is removing the Chrome browser from your devices.
✓ If Google is a spider, Chrome is its web.
"When you sync your Google accounts to Chrome, the data slurping doesn’t stop there. Information from other Google-owned products including its email service Gmail and Google search can be combined to form a scarily accurate picture"
Kate O'Flaherty, Wired Magazine, June 6th, 2021
“Why does a web browser need my financial data? I think that says it all really. I really struggle to think of a suitable justification for that.”
Security researcher Sean Wright, Forbes, May 20th, 2021
✓ For alternatives to the Big Three browsers, Firefox, Brave, and DuckDuckGo, do not collect or share any of your information
Switching from Google Maps to Apple Maps is another key move to de-centralize from Google. When granular detail about everything in your life is coupled with location data, it's hard to exaggerate the potential repercussions from Google Maps' data collection machine.
So powerful is this data, Google has been caught time and again lying and covering up its location-sharing practices. The company even engineered Maps to fool users into believing they could control and disable tracking when in fact, the function is always on whether you're using it or not and without regard for personal user settings.
✓ For a leveraged effect when moving away from Google, delete its Maps apps from your devices
We're sure to sound like a broken record by now, but it stands that one of the smartest and most effective ways to de-centralize from Big Tech is by refusing to use their email accounts.
We call it 'privatizing' and believe nothing is more critical for privacy and security today than taking back your inbox from Google and other "free" email accounts.
When you privatize email, you regain ownership and control of your personal information - now considered the "new oil" and the most valuable commodity on Earth.
We're big advocates for privatizing email as a primary strategy to avoid cybercrime and increase privacy, and it's one of the first things we do for a new client at TDS. More on private email, here, and for a deeper dive into why it's time to fire Gmail, here.
✓ For the long run, privatizing personal email is the most effective way to protect your privacy and personal information from Big Tech and avoid cybercrime and damages.
How's this for a fact of the month?
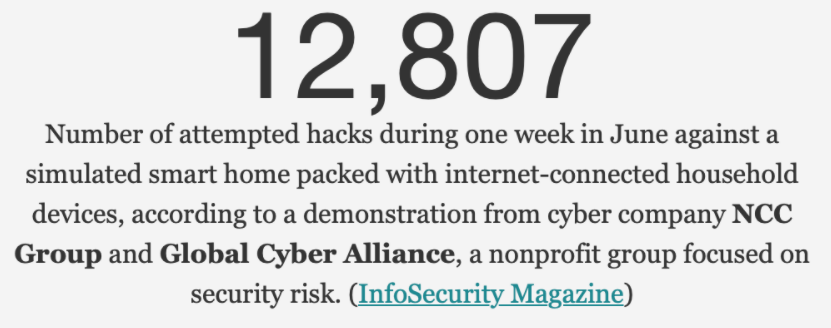
✓ Smart homes and offices are extremely vulnerable to hackers and cybercrime-related losses.
TDS's Managed Network Security service protects an entire network and all the connected devices from harm and anonymizes all internet activity for privacy. To test the security of your network, click ShieldTest.
Last month we introduced a new security product that combines device protection with a VPN. Fittingly enough, it's called Mobile Protection, and this is the first time we've recommended security for iPhones and iPad.
It seems the timing is just right when looking at some of the headlines in July:
✓ Upgrade - If you are a client and haven't upgraded from Freedome yet, click below for Mobile Protection with VPN:
Speaking of VPN apps, yes, they still drive us crazy, and yes, we still use them every day. We hang in there because the benefits of anonymizing on the internet are so worth it.
From a business standpoint, VPN apps make no sense for TDS. They require a lot of support and can frustrate users. It would be easier to just drop them from our product line, but we love our customers too much for that.
The pain users feel when adapting to a VPN is derived from learning. Perhaps unknowingly, they are developing skills to think critically about their digital presence and engagement. I don't know of anything more essential to our business mission at TDS. So we'll continue to advocate and support VPNs for all our clients, and we'll continue to work with developers to make them work better and easier to use.
In the meantime, we collect resources for VPN users on our support page here https://www.totaldigitalsecurity.com/support-resources/mobile-protection-vpn.
✓ A new link is on the support page with a handy VPN troubleshooting checklist titled "VPN won't connect? Here are 13 things to try.
Congratulations to our friend Eddie Marshall, Global Head of the Dentons Family Office and High Net Worth sector, for publishing his book:
"The Family Office: A Comprehensive Guide for Advisers, Practitioners, and Students."
Our contribution to his book is acknowledged for the cybersecurity expertise I provided. Eddie worked hard on this project, and we've always admired his work. Congrats Eddie! I just ordered the book on Amazon and will share some of it soon.
Finally, here's an interview I did in July with the Bradenton Herald on "Digital Vaults" - https://www.bradenton.com/news/business/biz-columns-blogs/article252932783.html

5 min read
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

9 min read
Over the past decade writing these letters, I’ve made it my mission to help you navigate the digital age with confidence and resilience. If I have...

4 min read
For generations, family offices and ultra-high net worth families have mastered the art of estate planning — preserving wealth, ensuring succession,...