5 min read
Meeting the New, AI-Enabled Face of Risk
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

The top question for my inbox in May was, “How can this happen?” How can a computer virus take down the biggest fuel pipeline in the country? The answer in the Colonial Pipeline case is consistent with most hacks, big and small; apathy. And in cybersecurity, like so much else in life, apathy is a killer.
The nature of cybercrime is less tangible than with traditional risks, and cyberspace is more abstract compared to “real life.” For these reasons, many still don’t grasp the realities of digital threats, and avoidance behavior isn’t uncommon with people and organizations.
Here's how apathy came to roost at Colonial Pipeline:
“We found glaring deficiencies and big problems ... I mean an eighth-grader could have hacked into that system.”
Robert F. Smallwood, whose consulting firm delivered an 89-page report in January 2018 after a six-month audit. May 13th, AP News
And this from the Wall Street Journal:
Colonial Pipeline Missed Security Review Before Hack
"Colonial ... didn’t undergo a requested federal security review of its computer networks when hackers hit on May 7."
WSJ May 26th
More and more hackers today find it easier to hack people than technology. Apathy and the "human element" are cybersecurity's weakest links, and every good hacker on the planet knows it. That's why email is usually the primary target of attacks - the inbox is a direct vector to their next potential victim.

Look at any of the most notorious hacks, and you’ll find email is likely to be the root of the problem. Even when you look more broadly at the hacks you don't read about; it's the victim's inbox where the trouble begins.
✓ It takes a self-starting initiative to break the bonds of apathy with digital risk, and the best place to start is by privatizing and securing personal email. Also, this is critical; always enable the email box's multiple-factor authentication (MFA) feature.
Before the Colonial hack, businesses and individuals have been paying ransoms for years without making the front-page news or getting help from federal and local governments. And while recent headline events include eye-popping amounts, we've seen victims extorted for payments as low as $10,000.
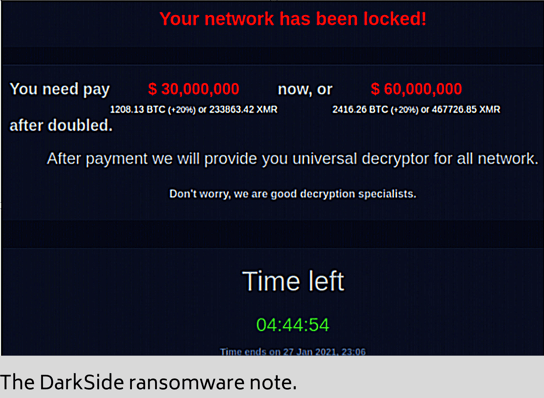
Let's look at DarkSide, the ransomware gang that extorted $4.4 million from Colonial Pipeline (with credit to cyber sleuth Krebs.)
"... much the same way McDonald's Corp. supplies local store owners with pre-made soft serve and frozen hamburger patties."
Bloomberg - May 12th, describing the business arrangement between criminal syndicates and their affiliates.
According to cybersecurity firm FireEye, DarkSide's affiliates fees worked with a sliding scale - 25% of ransoms under $500,000 down to 10% for ransoms over $5 million.
✓ To understand the risk of ransomware is to understand it as less as a virus and more as a business model.
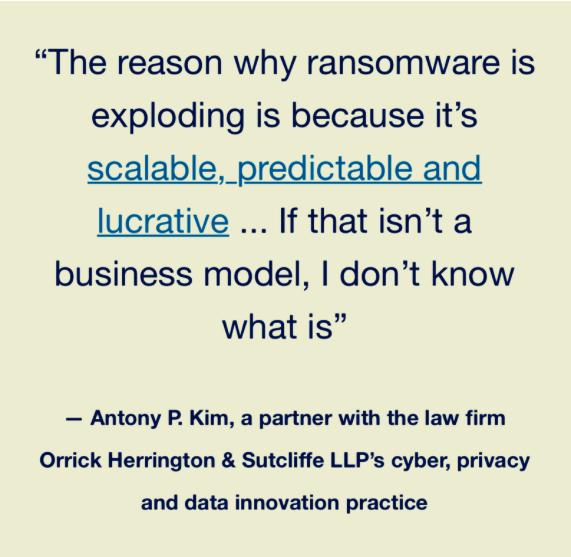
Cybercrime has been big business for a while now, and we've been writing about "the evolution of extortion" since 2014. But recently, ransomware has taken on a life of its own.
"In just a couple of years, cybersecurity experts say, ransomware has developed into a tightly organized, highly compartmentalized business."
The New York Times - May 29th
What the New York Times describes as' tightly organized and highly compartmentalized businesses' are in reality gangs of criminals enabled by a syndicate to push their malware around the world.
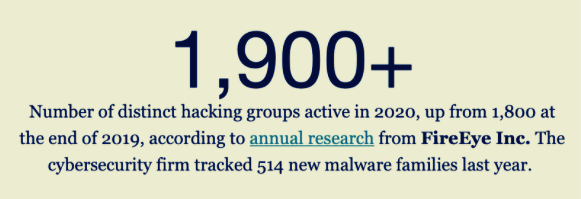
The syndicate scales its profits by arming affiliates of gangs with the best tools and services they need to be successful, including call centers and help desks.
“Any doofus can be a cybercriminal now. The intellectual barrier to entry has gotten extremely low.”
Sergei A. Pavlovich, a former hacker who served 10 years in prison in his native Belarus for cyber crimes.
For a spellbinding view into these organized cyber gang affiliates, read the article by the AARP, "Inside an International Tech-Support Scam."
Artificial intelligence is here and it will change everything in cybercrime.
"To date, hacking has exclusively been a human activity. Not for long."
Bruce Schneier - April 26th, "When AIs Start Hacking."
The outcome is predictable - AI coupled with the ransomware-as-a-service business model will drive growth in cybercrime and damages to unprecedented levels. Here's why.
First, AI doesn't approach problems as humans do. AI software used on stolen personal information will yield criminals with strategies and exploits they would have never found themselves.
Second, using AI to increase the effectiveness of the attack itself, anyone unsuspecting and unprotected is a ridiculously easy victim.
Bruce Schneier, one of cybersecurity's top gurus, says:
"When AIs start hacking, everything will change. They won’t be constrained in the same ways, or have the same limits, as people. They’ll change hacking’s speed, scale, and scope, at rates and magnitudes we’re not ready for."
Bruce Schneier, April 26th - "When AIs Start Hacking."
✓ We will see massive growth in damages as AI software is used with stolen personal information to commit cybercrimes on vast swaths of society.
The optimal solution for protecting from all cyber risk is to take a two-prong approach:
✓ You can check the security level of the network you're on right now in just 60-seconds, here - totaldigitalsecurity.shieldtest.com/
While the future holds many challenges, cyber risk is still manageable. Defensive technology is effective, getting better all the time, and AI is also on the side of good and enabling the cybersecurity industry to level the field.
✓ Nothing can eliminate cyber risk, but you can avoid most of it if you are thoughtful, prepared, and use best-in-class protection for your email, devices, and networks.
Here's my Quick Tip of the month for the Colony Group.

5 min read
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

9 min read
Over the past decade writing these letters, I’ve made it my mission to help you navigate the digital age with confidence and resilience. If I have...

4 min read
For generations, family offices and ultra-high net worth families have mastered the art of estate planning — preserving wealth, ensuring succession,...