5 min read
Meeting the New, AI-Enabled Face of Risk
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...
6 min read
![]() Total Digital Security
:
February 18, 2024
Total Digital Security
:
February 18, 2024

In February's blog, we delve deep into the core values of Total Digital Security, encapsulated in our commitment to provide an ecosystem ensuring optimal privacy and security across all devices, anytime, anywhere.
At the heart of our mission lie 'the fundamentals' — essential principles akin to the legs of a sturdy stool, without which our vision for a robust privacy and cybersecurity environment would be unattainable.
Let's embark on a journey through the key elements of our "Cybersecurity for Life" approach:
✓ First, here's a reader's guide to what follows next:
Step #1 - Find where the risk resides - "The Three Primary Attack Surfaces."
Step #2 - Determine a strategy to protect the 'Attack Surfaces' from cybercrime, ID theft, and loss of personal information - "The Four Fundamentals."
Step #3 - Identify best-in-class solutions for provisioning 'The Four Fundamentals' and implementing strategy with real-time tactical optimization 24/7.
✓ Before we explore the fundamentals in depth, let's first trace the path that led us here. With this, we aspire to construct a vivid 'mind-eye' view, enriching the reader's context and sharpening their critical thinking skills.
Our journey began with a user-centric approach, pinpointing three core areas of vulnerability:
To combat these vulnerabilities, we developed four indispensable pillars:
✓ We will detail the solutions and their benefits for each of the Four Fundamentals below.
Our approach is rooted in understanding the user's interaction with the digital world. By focusing on critical junctures of vulnerability, we identified '"The Three Primary Attack Surfaces" — the epicenters of cyber threats. This insight laid the foundation for 'The Four Fundamentals,' essential for constructing a universal privacy and security ecosystem.
Our identification of the fundamentals began with an 'outside-in' approach, starting from the user's interaction with the internet. This perspective enabled us to pinpoint cyber risk at its core, and we found it in three distinct areas. By concentrating on these critical junctures of digital vulnerability, we've articulated the essential fundamentals required to realize the vision of a comprehensive ecosystem of privacy and cybersecurity.
✓ Our analysis and insights reveal three primary vulnerabilities critical for anyone navigating the internet. These vulnerabilities are the epicenters of cyber threats, underpinning most successful hacks and cyberattacks. We've termed these critical points "The Three Primary Attack Surfaces."
It's simple, if not intuitive, but flagging these three culprits focuses our attention and creates a vivid visual in one's mind, which is essential for abstract issues like cyber. With this intelligence, we can effectively meet the risk where it lives.
1) EMAIL –
The #1 point of entry for cybercriminals and online fraudsters is email. Phishing, ransomware, spying, key-logging, and many other exploits start with an email. AI in cybercrime is increasing the risks inherent in email, and we need to be vigilant and on our toes with our inboxes more than ever.
2) DEVICES –
Computers, laptops, phones, pads, and tablets are vulnerable to viruses, data loss, malicious intruders, and much more.
3) NETWORKS –
More and more, home and office Wi-Fi and public Wi-Fi like cafes, hotels, and airports are considered "honeypots" by hackers.
✓ Understanding the risks inherent in "The Three Primary Attack Surfaces" guided us in developing "The Four Fundamentals," which constitute the indispensable pillars of a universally effective privacy and digital security ecosystem—seamlessly operational across all devices and networks, ensuring protection at every moment and location.
So, finally, here are "The Four Fundamentals of Cybersecurity for Life."
How to mitigate cyber risk and ID theft to the margin by creating an ecosystem of privacy and cybersecurity.
✓ More details follow below and illustrate how TDS solves these four fundamentals for our clients using advanced cybersecurity solutions.
* Benefits – email activities are off the grid of "free" email and embolden "digital identity." Security controls and intelligence with AI via Microsoft's email security platform.
* Benefits – a comprehensive, unified "full-stack" of endpoint protection to provide protection 24/7 with real-time optimization.
* Benefits – a comprehensive and unified platform for network security including firewall and VPN "as-a-service," off the public internet via a private "Point of Presence" or "POP," also called the "Gateway." Always on zero-trust state of security, identity-based access controls, AV at the gateway, DDoS protection, content and DNS filtering, and more.
See the illustration below: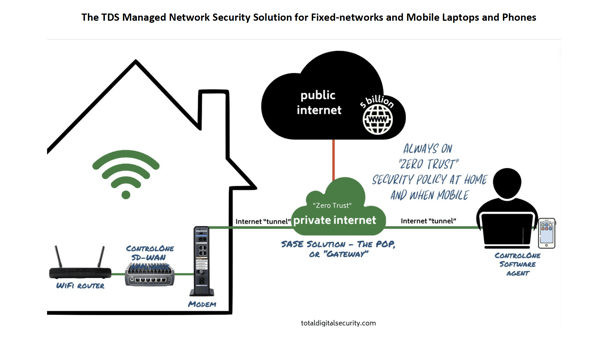
Security 'appliance' for homes and offices, and software 'agent' for securing laptops and iOS devices.
✓ The image above is a schematic of how the Managed Network Security by TDS works. On the left is a fixed-site network, and on the right is a user with mobile devices connected to a remote network, like public Wi-Fi, Starbucks, etc.
As we step into 2024 and beyond, it's clear that we've crossed a pivotal threshold in cyber vulnerabilities.
The fusion of artificial intelligence and escalating geopolitical tensions is not just increasing the number of cyber-attacks; it's also enhancing their complexity. This evolution in cyber threats is set to revolutionize our understanding of risk management, challenging its foundations.
The repercussions of this shift will be widespread, affecting individuals and large corporations alike, leaving no demographic untouched. The most alarming aspect? Our adversaries are exceptionally well-prepared and equipped. Backed by substantial investments over recent years, a spectrum of threats—from nation-states like China and Russia to criminal networks and lone wolves—stands on the brink, eager to exploit these vulnerabilities for disruption and gain.
Finally, we're excited to observe a pivotal change: approximately 50% of our new clients are now actively and preemptively crafting their internet security ecosystems.
Thanks for reading,
Post Script:
"Is our technology greater than our humanity?"
Senator Kennedy, R-LA questioning Big Tech social media titans, including Mark Zuckerberg, at a Senate hearing on January 31st.
"The Nexus of Disruption: In an era where rapid technological advancements intersect with geopolitical complexities, understanding the intricacies of emerging threats is paramount."
Kris Coleman, on the "Nexus of Disruption." Kris is the founder and CEO of our strategic partner, Red5. The firm's latest white paper: "2024 Global Security Outlook: A Nexus of Disruption," is a worthy read for security-related insights. Red5 has as much experience in the field as anyone, and the white paper brings insights into understanding emerging threats and the fast-evolving face of risk.
"We expect a twister of disinformation that with AI will make discerning fact from fiction increasingly difficult without the right tools and individual critical thinking skills."
Yours truly, on a webinar with a multi-family office group of executives and family members in January 2024. In the face of AI and its reach on daily life, discerning fact from fiction is a life-skill for survival and success today.
Our approach is learning new life skills for increased satisfaction, privacy, and security with personal technology.

5 min read
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

9 min read
Over the past decade writing these letters, I’ve made it my mission to help you navigate the digital age with confidence and resilience. If I have...

4 min read
For generations, family offices and ultra-high net worth families have mastered the art of estate planning — preserving wealth, ensuring succession,...