5 min read
Meeting the New, AI-Enabled Face of Risk
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

"Cyber Security in Real Estate Sales " begins by addressing three crucial questions:
Is cyber risk a real problem in the real estate sales industry?
Why is the industry being targeted?
How real are the threats for agents, brokers, and office managers?
And then answers three more:
How did it happen?
What does the future hold?
What can I do about it?

You don't need us to prove the problem. Just google some terms and see for yourself. Cyber risk is a real problem, attacks are growing in frequency and consequences, and many agents, brokers, and office managers are exceedingly vulnerable to the escalating risks.
While we won't spend any time throwing statistics and bombing you with numbers to prove the point, we will include this quote made recently by the legal department at the NAR:
"Cybercrime against large retailers like Target and Home Depot has cost these companies millions in damages. Now, cybercriminals are targeting the real estate industry ... they specifically target people in the real estate industry ... skulking in the background, watching all the information going back and forth."
Jessica Edgerton, Associate Counsel – National Association of Realtors, June 22nd, 2016
In the minds of cybercriminals around the world, not only is real estate where the money is, but it's where the BIG, EASY money is.
|
 |
Real Estate Sales It's Where the Big, Easy Money Is in Cyber Crime. |
The risks are stacked and multi-fold - encompassing most every element of the broader term "risk".
Going forward, it is impossible to discuss any element of risk without considering cyber-risk in the dialogue.
 |
 |
What does this look like in the real world?
Here's a recent headline:
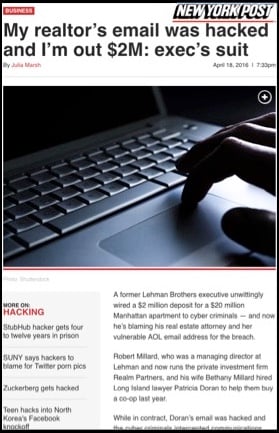
Even masters of risk don't have their eye on the ball that is their #1 risk today - personally, professionally, and across all facets of life.
For more on the breach:
How did your personal information become the most sought after commodity on the planet and under relentless attack by cybercriminals from around the world?
Interestingly, understanding the answer provides clarity for the future, and provides answers to our problems.
Simply, it can be explained by the convergence of three, game-changing trends that are affecting virtually every element of our lives.
Here's the movie:
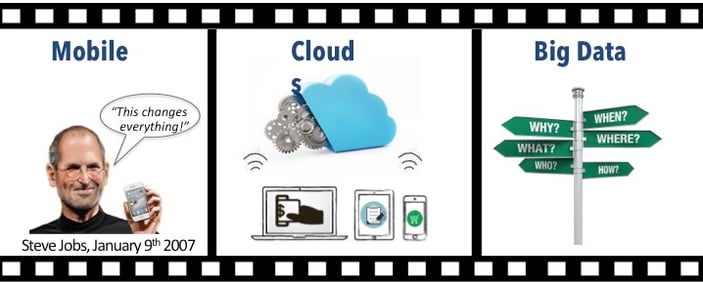
Shortly, 80% of the world's population will have a supercomputer in their hand in the form of a smartphone.
Billions of users on their smartphones are connecting to the world's information, creating ever more information at astounding rates.
And, Big Data software sorts, sifts, and mines the data for knowledge.
Knowledge = Power = Wealth.
So, how does information become big money?
Digital Alchemy - From Bits to Bullion.
Why cybercrime is so profitable and will dwarf all other crime and risk.
 Does anyone know why there is a slide here with an old man holding a pigeon? Anyone?
Does anyone know why there is a slide here with an old man holding a pigeon? Anyone?
Read it here:
http://www.totaldigitalsecurity.com/blog/from-bits-to-bullion-the-alchemy-of-cyber-crime
Spoiler alert - but you probably already know it's going to get much, much worse.
We predict 3 to 5 years of the Wild West, unlike what you can probably yet imagine.
Here's why:
The IoT - The Internet of Things, is a complimentary mega-trend that will accelerate the volume of information and distribution into warpspeed.
And, digital currencies like BitCoin are driving professional criminals online; now able to steal, defraud, extort, and blackmail for loot that is anonymous, portable, and immediately liquid into any other form of wealth they choose.
Pause to ponder that.
The convergence of IoT, Digital Currencies and BigData software technologies is a potent blend and inexhaustible fuel supply for a rocket-booster launch to all elements of crime, and at a pace and to a level never seen before.
The criminal motive may be unlike any other in history.
Then, ...
... perhaps the cycle peaks. When the momentum shifts, and the "trade" is neutralized.
The "trade".
It's an absurdly profitable, safe, and easy trade - and it created some of the world's largest fortunes over the shortest periods of time in history. Read more about the arbitrage trade of your privacy and personal information:
http://www.totaldigitalsecurity.com/blog/how-to-be-a-billionaire-by-25-arbitrage-privacy
Neutralization will come in the form of increased digital autonomy by the surviving class, and broad government reforms and its socializing of protective responsibilities.
How much $$ can you make on "the trade"?
Fortunately, there is a lot you can do about it.
The key word here is "you".
Your risks are more important to you than to the IT department. Federal and local governments are way behind, and their technology is decades old. Law enforcement? You don't want to find yourself in that spot.
The really good news is that cyber security has become a big business in the last few years, and fresh investment capital is disrupting the industry with better, easy to use, and affordable technology that is highly effective at protecting for the risks at hand.
Here's how to use it:
The Four Fundamentals of Cyber Security
For a state of greater control over your information and digital footprint, and to achieve Cyber Security for Life, we frame the issues with "The Four Fundamentals of Cyber Security."
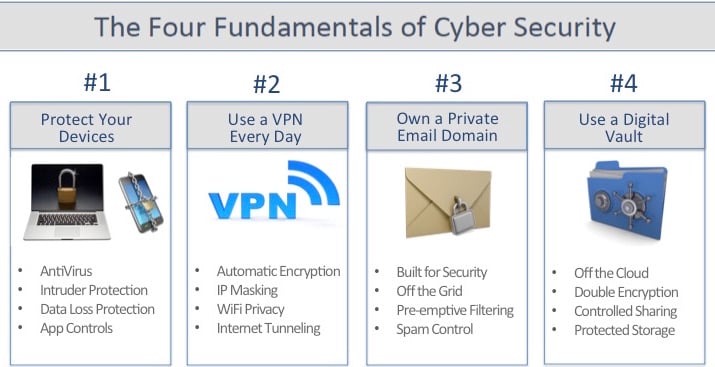
http://www.totaldigitalsecurity.com/the-four-fundamentals-of-cyber-security-for-life
|
Control your technology, or it will control you. Act as a leader toward awareness and best practices. Personalize the issues and don't leave it to the IT department, government, or corporation to protect you. Focus on individuals using their own technology in perimeter operating environments. Position yourself to benefit from the innovative technology being developed in personal IT security today. |

5 min read
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

9 min read
Over the past decade writing these letters, I’ve made it my mission to help you navigate the digital age with confidence and resilience. If I have...

4 min read
For generations, family offices and ultra-high net worth families have mastered the art of estate planning — preserving wealth, ensuring succession,...