5 min read
Meeting the New, AI-Enabled Face of Risk
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

RANE - the Risk Assessment Network Chief Marketing Officer, Greg Radner, interviews Total Digital Security CEO and Founder Brad Deflin, on "Improving Cybersecurity for the Private Client" for their April 2019 podcast.

An introduction by Greg Radner
"Cyber risk continues to migrate from exclusively large enterprise environments to individual users and their personal technology and internet-connected devices. Additionally, the threat landscape is changing from primarily targeted attacks to mass-opportunistic campaigns that exploit unaware users and under-protected devices and networks.
In this podcast, RANE CMO Greg Radner interviews CEO and Founder Brad Deflin at Total Digital Security, where his firm specializes in providing enterprise-grade cybersecurity solutions to protect individuals and their personal technology from cybercrime.
Total Digital Security offers enterprise-grade cybersecurity solutions to individuals, families, homes, home offices, professional practices, and trusted client advisors. Solutions are remotely monitored and managed for real-time protection using multiple intelligence databases, automatic updates, and machine learning for optimal performance. Recent enhancements include artificial intelligence to address zero-day threats, and real-time updates that occur within 60-seconds of new threat discovery."
Listen to the podcast, here:
https://soundcloud.com/user-428199630-625456398/improving-cybersecurity-for-the-private-client
Greg:
Welcome Brad, I'm glad you could join us today.
Brad:
Good morning Greg. Glad to be with you.
Greg:
So, we are seeing this migration (of cyber risk) from enterprise to personal and it's really sort of the invasion of cyber risk and this trend towards mass opportunistic attacks. Talk a little bit about your data and observations that you've got from actively being the space.
Brad:
Sure. So, the company was founded on this mega-trend really where the risk was migrating away from exclusively the enterprise IT department managed environments, which are still targets of attack of course, but increasingly attacks are aimed at individuals using their personal technology. There's less awareness, they are more vulnerable, and yet they are still where the money is and there is a good profit motive involved.
And now, with so much information having been stolen say since 2013 when we had the Home Depot and Target attacks and then all the headline breaches - if you notice, what they're after is our information. It is proportionately less and less about intellectual property, it is less about cyber warfare or spying on whether it be corporate government or military entities, and more of getting our personal information so that it can be assembled into datasets and pulled in a way where mass exploits can target many thousands, tens of thousands and more targets at the same time - but actually targeting in a customized way to each individual according to the information that they may have on record and that they're pulling from their data sets.
So, since we started in 2013, cybercrime for profit was about 50% of the overall problem. If you think of cyber risk as a big pie and that pie predominantly before 2013 again was around cyber warfare, intellectual property theft, cyber espionage, really not necessarily cybercrime for immediate profit. In 2013, then the game began to shift. While the pie was smaller in 2013 than it is today, the cybercrime for profit element which was more around the mass opportunistic-type exploits reached 50% of that overall pie.
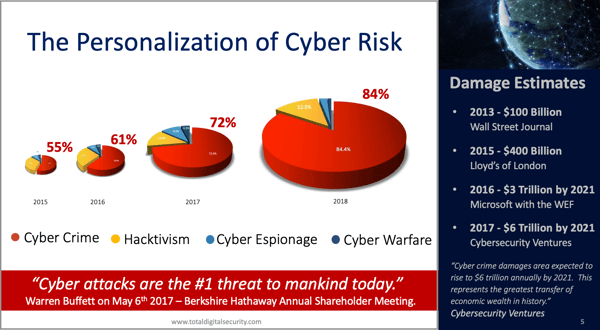
Now the pie is many, many times larger. For perspective, the cyber-attack pie the overall issue the overall problem in terms of damages from cyber risk was about a hundred billion dollars maybe in 2013 now that number is estimated to be in the trillions and yet the cybercrime for profit which again is mostly around mass opportunistic campaigns is almost 90 percent of the activity so not only has the overall activity expanded tremendously but the portion that is targeting mass individual personal users of technology has been the real driver of that overall growth
Greg:
Yeah some scary statistics there I'm actually calling into this podcast from the SecureWorld Boston conference today and one of the sessions they were talking about a use case where someone's phone was really accessed because they were letting their children use the phone to play games and the games themselves had a vulnerability that allowed you know an adversary to get in through the game and then actually get into the network through their email access so it was an interesting use case I'm sure you've got some cases and examples from clients that you've worked with that you can share with our audience.
Brad:
Yeah, and that is an example that we see more and more of where the kids might use the device and they might access some questionable sites some sites that might be posing as a gaming site but have another agenda a criminal agenda behind it and eventually the device is compromised and some other exploit begins to take place that we're very much seeing that out in the field.
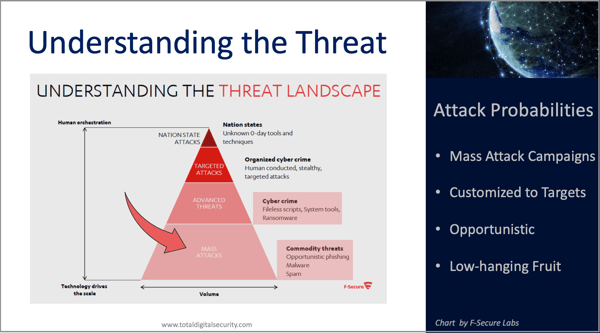
You know, we exist at the intersection of people, the technology they use every day, and what we call the new face of risk. The new face of cyber risk is not so much in a data center or an IT department but out there in the field at that intersection where the rubber really hits the road in terms of the activity that we're talking about.
Another thing that I think is interesting and that people should be aware of is the level of patience that hackers and cyber criminals have these days. You see statistics all over the place and one of the recent ones was a hundred days on average skulking in a device to monitor the activity back and forth. I've seen other estimates that are higher whatever the number is you were finding they're very patient they're applying software that monitors the activity collecting that data using smart software to organize and assemble that data to pick their spots in order to optimize and get the most out of the exploit that they can.
An example from the field is a gentleman came to us 52-year-old businessman from South Florida and he woke up one day and three of his investment accounts held it three different firms all three were wiped out and after some forensics and bringing a partner into the case that is an expert on forensics we determined that they had been skulking in his environment in his technology environment for almost six months. Maybe they could have you know breached one account earlier, but they took their time they were patient they knew there were three accounts they waited to get those credentials. They picked their spot they optimized their attack and those were the results that he had.
Greg:
Great examples you know so there's really not that much separation some of these examples between our business and personal lives and so how do you bring sort of enterprise-grade cybersecurity to the private client or to individuals What's the process innermost a value in doing so and you can comment.
Brad:
Sure, yeah so conceptually we started the company in 2013 based on two what we called bankable trends - two trends that we felt were very predictable that we felt were not difficult to extrapolate what was happening and built the business based on those two bankable trends.
Bankable trend number one - we already spoke about is the personalization of the risk the migration of this risk into environments that were totally unprepared. The other bankable trend number two is really the other side of the coin and that is tremendous capital coming into the IT security industry which was you know historically kind of a stagnant industry not a whole lot of innovation. Some large government military type customers not much of a consumer demand. That really changed beginning in 2012 - 2013 when it was recognized IT security is a great growth industry for the future.
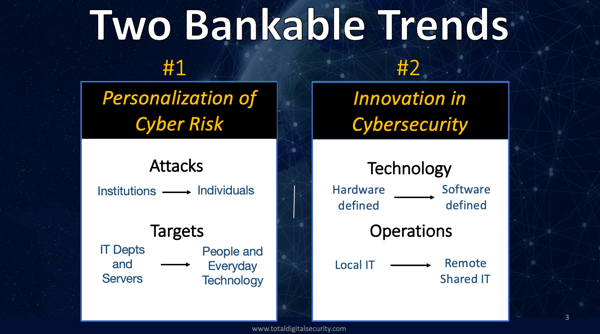
If you remember the environment in 2012 or 2013 there weren't a whole lot of growth prospects in the world at that time - after 2008 and the financial collapse. However, there was still an awful lot of capital with low rates and Fed-induced liquidity there was a lot of investment capital and a lot of that capital found its way into the IT security industry, and much of that capital was way down the capital stack – in venture capital, startups, companies backed by large amounts of capital and very smart people, innovative people with innovative ideas we're starting with a fresh slate. They could use advanced networking technologies, advanced software technologies, including artificial intelligence which was just coming into its own at that point in time, to disrupt the sustaining players in the industry that were more around selling hardware. Selling boxes, as they say, versus selling results which is really what people want.
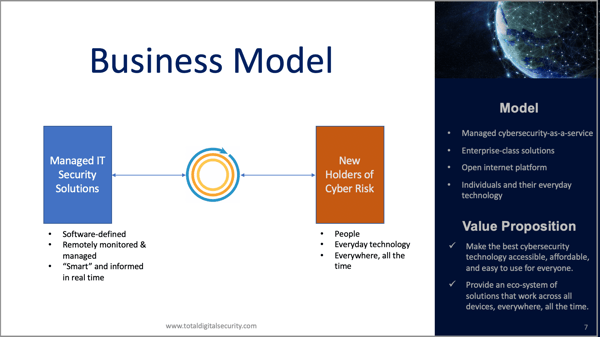
Results-as-a-service, if you will, and a lot of that focus from that capital was around users and devices because that's where the activity was migrating to. So we concluded that we could tap into that innovation, find the solutions that were built for mission-critical environments but were software-defined, remotely monitored and managed, using advanced machine learning and artificial intelligence as tools and deliver that all the way to one user in one device or a family or a home office or a professional practitioner. They could receive the same level of protection as a large enterprise in a very affordable and simple to use fashion. So that's the approach that we've taken, and it started in the ultrahigh-net-worth segment as they are risk-sensitive, and once we explained our value proposition and explained what we were doing we got really good traction there.
 However, the solutions are affordable enough and the problem is big enough that that market is expanded and we handle for example individual Realtors, real estate agents right that may not have an IT department that is making sure their devices and their practices are protecting their clients and their reputation and their brand out there in the field and really everything in between. The billionaire family with multiple residences, again all the way to the individual with a of personal devices that simply wants to protect from this risk.
However, the solutions are affordable enough and the problem is big enough that that market is expanded and we handle for example individual Realtors, real estate agents right that may not have an IT department that is making sure their devices and their practices are protecting their clients and their reputation and their brand out there in the field and really everything in between. The billionaire family with multiple residences, again all the way to the individual with a of personal devices that simply wants to protect from this risk.
Greg:
You probably created a new term you may want to trade ark: Results-as-a-service. You created something new I think that's an awesome term.
Obviously if you're working with individuals and everything it's got to be easy to use can't disrupt their you know current way they work it's this or it's just not going to work like it might be more disruptive in in in an enterprise environment then it's got to work you know everywhere and all the time everywhere they are you know it's always kind of on so talk a little bit about this open platform model that you've got and how you how that works and how that can really help with this always-on everywhere kind of approach
Brad:
You said it earlier, Greg, there really is no line of demarcation anymore between our personal lives, our professional lives, what we're doing individually what we're doing for as a trusted adviser we're sort of on and connected everywhere all the time. So it's an existential issue and our value proposition and our mission statement includes to “Provide solutions that work everywhere all the time across all of our devices just like we do.” And so, the solutions have network ubiquity regardless of where you are you have a connection to a data center that is in real-time protecting your activities protecting your devices protecting you from the outside, anonymizing you as much as possible in your activities whether you are on your phone or your laptop or your home computer, or anywhere in between.
It’s really important for the private client that these things are not disruptive, that they are seamless, however I'll tell you that it's been really interesting and very rewarding actually in terms of you know people have very little appetite for the issue there's a lot of avoidance behavior a lot of apathy but there's also a swelling desire for empowerment. Nobody wants to be bullied, nobody wants to be a victim, and people do want to embrace the Internet for all of all its worth, so once they start using the solutions and they start you know tapping in to see what's going on. They don't have to do anything, but they're still informed, they still recognize the value based on results, and so their level of curiosity increases and their level of engagement in the matter increases. Now they are noticing the headlines more, they're tuning in, and so the awareness level and the behavioral adaptation level goes up significantly I think as a result of being a user, a consumer of the solutions. So it drives both ends, which I think are really important for the ultimate level of defense - to have an informed, aware, and interested user plus best-in-class solutions both of which or on all the time again wherever you are and whatever device you happen to be using at the moment.
Greg:
Yeah, it's great. I mean the whole issue of just increasing awareness of the issue I think it's a big lot of sort of hurdle I think in this in this kind of marketplace another session that was earlier today at this conference talked about our mobile devices being the real next attack vector and people tend to not think about that they're doing everything that it might feel on their computer but they're doing it through their phone people don't necessarily think about that as an attack vector and maybe just a building the awareness of that it's half of the battle.
Brad:
That's a really good point Greg so you know we talked about the mobile revolution which I think was launched the day in 2007 in January when Steve Jobs introduced the first iPhone, right? We didn't know if Apple was going to come out with a phone and there was a lot of anticipation and Jobs by then with a real hero and so everybody was tuning in and sure enough - he introduced the first iPhone.
What he (Jobs) said was prophetic. He pointed to the iPhone, he looked into the camera, and he said “This changes everything.” He wasn't talking about the iPhone. He was talking about the smartphone, and he went on to say “A supercomputer in the palm of your hand.” which is very much the case.
As we go forward in time and advances keep coming it is even more in more the case - more people have a supercomputer in the palm of their hand on our planet than have access to a clean toilet. That's how fast and how broad this mobile revolution has taken place. And then he finally said; “Your life in your pocket.” That’s what we're doing - we're hubbing our lives around our phones, around our mobile devices, we want to do what we want to do on the internet wherever we are anywhere, anytime. Whether it be banking, shopping, browsing, emailing, communicating, chatting - you know all the different elements of how we are hubbing our lives around these devices. So, our mobile devices our phone are rich with the kind of information that fuels the exploits of hackers, and again because of the lack of awareness and because of the vulnerability of these devices without any sort of protection and protective solutions that is increasingly the target around the world.
Greg:
You know one thing we haven't touched on, and which we hear a lot about when working with corporations, is the whole issue of privacy. In particular, you're looking at next-generation age folks that's a big concern and they have a sort of uh probably a heightened appreciation of some of the privacy issues that said they often putting a lot of their personal information out on the web maybe even to talk a little bit about how your solution addresses some of those issues and maybe some other concerns next-gen folks might have.
Brad:
I think it's (privacy) a real important topic and anybody in a leadership position in a position of influence and a private domain public domain whatever the case is I think really needs to start to take it a stand on these things. In the U.S. especially our regard for privacy is so low and our attention to the value of our personal information is at the point where you know the younger folks they're really great at using the devices but when it comes to thinking about the issues of privacy, when it comes to the elements of personal information, it doesn't cross their mind. In the U.S. we have been snookered into believing that everything on the Internet should be free. But let's look at the 25 year old or 30 year old billionaire - in many cases these young innovators have created their wealth faster and greater than in any other time in history and in most of those cases it's because they're giving you something for free over the internet, whether it be Facebook or any other applications that we can think about and actually that's an arbitrage. These are very smart operators that really understand the value of your privacy, the value of your personal information, and will give you a service for quote-unquote free exchange for that and that arbitrage is creating some of the greatest wealth faster than any other time in history.
So we have to ponder that, and we have to put that into perspective and share that notion so we're not left with a couple of generations that are entirely unprepared for what can happen as a result of operating on the internet without a lot of thought to the potential consequences. Everything they do you know is written in stone when it goes out to the internet, it's one way, there's really no getting it back, and with advanced software these days being able to mine tremendous volumes of information to create the story that somebody might want to use against you is very easy.
Whether it be; applying to a school, or employment, or your reputation whatever the case might be, we have to be a lot more thoughtful about how we put these things out there and start talking to the next generation about that. Our work, we say, goes from the boardroom to the break room, to the living room, and so we have spent a lot of time in the living room talking with the next generation and their parents and dealing with family offices to try to figure out how do you influence these kids to care. Because, you know, at the end of the day there is very little understanding or care for the matter. One way that we have found to be especially influential is by creating a family email domain. So you take your family name or some semblance of it, some domain name that might be available; myfamily.com, or you know, come up with a domain name. You privatize it so it's not in the white pages of the internet. You create email boxes for your family and the parents start to insist to the kids “…if you want to talk about money, or grades, or travel, or education, or healthcare, or any of these sensitive issues, you know we're going to insist that you use our family domain.”
It's a multi-generational, cyber safe room for the family to use. What happens is kids while they roll their eyes at the front-end, start to think every time they use that email “…now why is this important to mom and dad?” … and they start to get into a habit. Their awareness starts to click in, they might like the vanity element of it, but you know even in my own family I have three kids and just because I'm in the business doesn't mean they necessarily care more about the subject, but we have seen that it’s a driver of results and a driver of influence to begin to think differently. And then you can start talking about VPNs, and device protection, and best practices with passwords. And you know, you can position that in a way that again is empowering - more about “… here's why we think we need to think differently, here's what it can mean for you, and let's use it to our advantage.” It's not a consequence, but it's an empowering positioning that seems to make a difference with this next generation issue that we face in the US.
Greg:
Yeah, it really hit home - your comments on time as a father of three girls, I have seen the eye roll many times so and this whole idea of sort of how you position it of a culture of the family office or the private client I think is a big one.
I've heard you talk about “Cybersecurity-as-a-Employee Benefit” as another way of kind of positioning and building that cultural change you know across all of them - can talk a little bit more about that?
Brad:
“Cybersecurity-as-an-Employee-Benefit” - this started when we were invited into businesses - private, public businesses to talk to employees and teams and sometimes subsets of executives about the issue. We explain why it's happening, how it's happening, what we can expect in the future, and what we can do about it. And so we started to get feedback immediately, really positive feedback that was “… hey you know thanks for that, you know the IT department came in and they wag their finger, and say don't write down your passwords. And you know the FBI came in, and okay we get it it's a big deal, but you actually told us what to do about it.” That was really helpful so that morphed over some period of time into what we call “Cybersecurity-as-an-Employee Benefit.” We don't position it as a consequence of the compliance department, or the regulatory, legal HR issue. We talk about it as empowering individuals for survival and success in the digital age.

You know, we are in the transition phases of coming into a whole new era for mankind and it’s in these first innings that are so problematic. It's in these first innings that determines the next generation that haves and have-nots. Presenting the subject in a way that prepares the individual whether they're in the workplace or out of the workplace, because again these are existential issues, it gets their attention and causes them to internalize the issues personally, which creates you know an ROI back to the enterprise because if they're internalizing it personally and they're adjusting their thought processes their awareness level their behavior - that will come back to the enterprise. So the next generation was where we not only did the inform, educate, and empower sessions workshops and boot-camps, but we also brought in real solutions that were subsidized by the company or the sponsor of the event. So first we inform, educate, and empower change to get their interest and energize the room, and then we bring forth real solutions that they can begin using immediately on their devices in their personal life to mitigate this risk.
When we are able to measure the impact from an ROI standpoint, it's really quite dramatic. We call it the “hermeneutic circle”  - when you can apply eye-hand, time-motion, and muscle-memory with knowledge and information, the level in the rate of adaptation takes on a whole new arc compared to maybe some of the more traditional approaches.
- when you can apply eye-hand, time-motion, and muscle-memory with knowledge and information, the level in the rate of adaptation takes on a whole new arc compared to maybe some of the more traditional approaches.
Greg:
Brad, before we end you know it seems like a lot of people take the approach that well it's going to happen you know why should I put all this energy into it you know there's a bit of helplessness on it a little bit and that that's preventing people from taking the next step. What and how would you respond to someone with that has got that approach today?
Brad:
That’s really what we see all day, every day in the field.
People are daunted. People are overwhelmed. People are struggling to figure out how to think about it, if they even try to think about it. So they are left really kind of flat-footed at a time when it's really important to start to think about change.
So the message is this; the solutions these days, that is the cybersecurity solutions that are in the field now, and available in a highly affordable, simple-to-use way, are incredibly effective. They will continue to get better cheaper and easier to use because that's what technology does. So we should position ourselves on that arc of getting better, easier to use, and more affordable, and bring them into our lives because they make a substantial difference.
If you think, and we know that the predominant activity, 90% of the activity, 90% of the risk plus is around opportunistic campaigns - looking for the low-hanging fruit, looking for those that are vulnerable and not prepared. If you can simply get yourself off of that radar screen as a result of having some of the most basic solutions, you have eliminated, or avoided at least, a tremendous amount of the risk. And again, that notion can be very empowering once people understand it.

When I was in compliance and supervision in the financial services industry, I remember a mentor of mine saying “Brad, you can't expect people to comply with what they do not comprehend.” So we have to start it with informing and educating people in a way that makes sense to them individually - as individuals - and with that, you get their attention and introduce solutions, and that's where you mitigate this risk really all the way down the line to the point where it becomes far less of an issue going forward and positions these people for these significant advances and improvements in the solutions that we're seeing coming ahead.
Greg:
That was great! I learned a lot, I'm sure our audience did too, and I just want to thank you for joining us today.
Brad:
Thank you for having me Greg I enjoyed it.
Contact Total Digital Security for cyber risk solutions, services, and education.
Topics:

5 min read
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

9 min read
Over the past decade writing these letters, I’ve made it my mission to help you navigate the digital age with confidence and resilience. If I have...

4 min read
For generations, family offices and ultra-high net worth families have mastered the art of estate planning — preserving wealth, ensuring succession,...