5 min read
Meeting the New, AI-Enabled Face of Risk
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

Family offices are finding the emerging risks related to cyber security as particularly challenging. Even by today's standards, the online environment is especially hostile for a family office, its clients, employees, and vendors. This week's report discusses why the risks are stacked against the family office, what the future holds, and how to strategically address the issue for the long-term, in spite of the rapid changes in technology and the constantly evolving nature of online threats.

1. The Family Office is Being Targeted
Criminal hackers understand risk vs. reward. Family offices are considered prime targets for cyber attacks because the environment is rich with upside opportunity, and considered low-hanging-fruit in terms of difficulty and risk of attack.
Lucrative, Multi-Dimensional Target - "Because it's where the money is." The family office environment is a "honey-pot" target, with many layers of valuable information and criminal opportunity. With a single breach, the perpetrators can gain access to personal and identifying information, health care records, tax returns, bank and brokerage accounts, and information about employees, vendors, and business associates.
Lack of Preparedness - It is generally understood that there are insufficient defenses to protect the rich information a family office will likely hold.
2. The Risk is Stacked at the Family Office
Family offices must recognize, manage, and mitigate 3 layers of risk;
Compliance and Audit Risk - A family office may or may not be regulated under the Advisers Act, but many may still be subject to PCI and HIPAA regulations for privacy and security. If an office handles credit card transactions or electronic healthcare records, it is potentially subject to Federal and State compliance requirements.
Client Expectations - The primary role of a family office is risk management and mitigation. Clients and beneficiaries are expecting information and guidance, and it's crucial to address the matters of cyber-risk, define accountability, and manage expectations.
Reputational Risk and Network Damage - Professional, trusted advisers are beholden to their reputation. The matter of cyber-risk is well known and we have plenty of evidence concerning the potential fall-out from a breach. The level of patience and forgiveness for an unprepared entity or individual is quickly dissipating.
3. Clients and Beneficiaries Are At Risk
The face of risk has changed dramatically in just the last several years. How and why has this taken place? We identify these primary, secular drivers:
Mobile - the fastest-spreading technology in humanity's history has deepened and broadened mainstream engagement with online technology.
The Cloud - mobile has driven data to the cloud, spreading personal information everywhere.
The Stalker Economy - some of the largest fortunes in history have been built in the shortest amount of time by arbitraging our personal information. See: "How to Become a Billionaire by Age 25."
Digital Currency - anonymous, portable and liquid transfer of wealth is driving criminal cartel activity to the internet.
Big Data - powerful, accessible and inexpensive, BigData software is empowering criminals by giving them the ability to quickly manipulate vast amounts of data.
IOT, The Internet of Things - our future invariably holds a surrounding of "smart", connected devices, products and services, vastly increasing the attack surface for online crime.
Over a very brief period, these powerful trends have converged to fundamentally and permanently alter the risk surface of regular individuals, families and businesses.
4. The Democratization of Cyber Risk
The internet has successfully democratized cyber risk and now, the greatest threat lies not with IT managed, server-centric architecture, but with the individual, fringe environment of the network.
"Rather than a 'Cyber Armageddon' scenario that debilitates the entire US infrastructure, we envision something different. We foresee an ongoing series of low-to-moderate level cyber attacks from a variety of sources over time, which will impose cumulative costs on US economic competitiveness and national security."
James Clapper, U.S. Director of National Intelligence. "Worldwide Threat Assessment of the US Intelligence Community" report presented to lawmakers on Feb. 26th, 2015. "
For criminal cartels, hacking is the crime of the future. It's more profitable than the drug trade, far lower probabilities of consequences, unlimited upside, and loot that is anonymous, instantly portable and perfectly liquid.
5. Family Offices Need Innovative Answers and Solutions.
For decades, a handful of providers that form the incumbent supply chain have had little incentive to innovate due to their domination of the sales channels. Now, regulators and consumers are demanding better and Wall Street and Silicon Valley have responded. Significant capital investment by VC’s and cyber-related M&A transactions are resulting in increasingly effective and innovative products and solutions that are disrupting the incumbent providers.
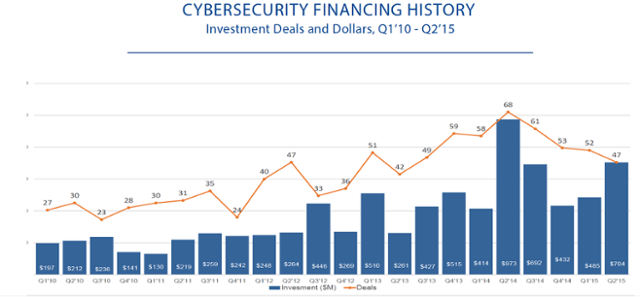
Today, "smart", software defined, cloud-enabled technologies, are usurping hardware and disrupting traditional IT solutions providers with better, easier and cheaper solutions that are sold "as a service". Long-term contracts, service obligations, and brand commitment are no longer required, and as the internet democratized cyber risk, so has it democratized its risk management and mitigation. Now, the most vulnerable aspect of cyber risk can be managed with state-of-the-science solutions that protect everywhere, all of the time, simply, and affordably.
For individuals, families, professionals and other small groups, Total Digital Security is the leading resource to bring these technologies to effectively manage and mitigate the dynamic risk environment we face today, and will continue to face well into the future.
"Cyber Security and the Family Office." - Presentation to the Association of Financial Professionals Annual Conference 2016.
Please contact us at 1-877-643-6391, email info@totaldigitalsecurity.com or click:

5 min read
When we introduced our OmniNet Bridge solution in 2014—known to many of you as My Digital Shield—it represented the next generation of network...

9 min read
Over the past decade writing these letters, I’ve made it my mission to help you navigate the digital age with confidence and resilience. If I have...

4 min read
For generations, family offices and ultra-high net worth families have mastered the art of estate planning — preserving wealth, ensuring succession,...