June Letter
Hi there,
Recently, from our vantage point in the personal cybersecurity business, threats and damages from email are spiking.
 Over the last 60 days, we've seen well above average cases of "email spoofing" with some losses well over $100,000 each.
Over the last 60 days, we've seen well above average cases of "email spoofing" with some losses well over $100,000 each.
Email Risks
Unlike ransomware, cybersecurity products cannot prevent loss from "email spoofing." With spoofing, protection relies entirely on the recipient of the email - the person using their inbox.
Only an informed and aware recipient of the email can prevent damages from most email attacks today, and hackers are increasingly betting you aren't one of them.
Which is why:
 Over 90% of all cybercrime starts at the inbox and most damages are due to the recipient's own actions.
Over 90% of all cybercrime starts at the inbox and most damages are due to the recipient's own actions.
Email Spoofing
The goal of email spoofing is to make the receiver of an email believe the sender (the perpetrator) is someone else - a known and trusted party being the source of the email. Then, assuming the recipient perceives the contents in the email body as credible, unwittingly takes action that furthers the crime.
Understanding email domains and spoofing requires abstract thinking, and sufficient explanation is beyond this letter's scope. So, the following is less about how it works, and more about how to protect yourself.
There are a few versions of email spoofing. The variations we see most in the field are Look-alike Domain Spoofing and Display Name Spoofing.
 These two strains make up over 96% of all email spoofing attacks and are the versions I'll address here.
These two strains make up over 96% of all email spoofing attacks and are the versions I'll address here.
Look-alike Domain Spoofing
An early version of email spoofing is the "look-alike domain." You've likely seen them before; the sender's email address shows a domain name very similar to the one you know and trust. But, it's just slightly off, with a character reversed or other illusion to trick the recipient.
A simple example:
mylocalbank.com is spoofed with a look-alike domain: mylocalbanc.com
 Earlier this year, a charity lost $1 million to a look-alike domain email spoof.
Earlier this year, a charity lost $1 million to a look-alike domain email spoof.
Display Name Spoofing
On the rise recently is a more sophisticated version of email spoofing known as "Display Name Spoofing."
With the Display Name Spoofing approach, for the recipient at the inbox, it appears the domain name is accurate, the sender's email address is correct, and everything, including the content of the email, matches expectations.
The screenshot below is an example of Display Name Spoofing from my inbox.
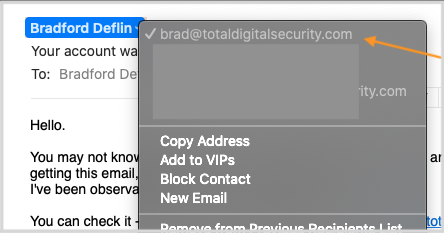
The email from the image above arrived in my inbox and appeared to be from myself.
Clicking the display name field, which is showing my name "Bradford Deflin," opens the dropdown list to identify the sender's email address. In a Display Name Spoof, the sender's actual address is masked and replaced with an address the recipient knows and trusts.
In this case above, the hacker wanted me to believe he hacked my account and the email was coming from my own email box "brad@totaldigitalsecurity.com."
Click here to see the entire spoofed email, including the hacker's instructions for paying the extortion demand to his BitCoin account.
 I believe Display Name Spoofing is fast becoming the most insidious and potentially damaging email-related risk today.
I believe Display Name Spoofing is fast becoming the most insidious and potentially damaging email-related risk today.
How to Protect from Spoofing
With stolen personal information and a little research, a hacker using the Display Name Spoof can engineer and customize an email attack that can fool anyone.
In the video below, I use real-world examples including from my own inbox, and explain how to avoid being a victim of email spoofing using your TDS webmail email tool.
https://youtu.be/AgNcmUA6FgA
 TDS Private Email Customers - your webmail includes a tool for helping you identify suspicious emails, including spoofed emails.
TDS Private Email Customers - your webmail includes a tool for helping you identify suspicious emails, including spoofed emails.
What is TDS Doing to Prevent Spoofing
Cybersecurity technology is advancing to help email users determine the legitimacy of messages in their inbox. Here are the specifics:
SPF - Sender Policy Framework - is an email authentication method designed to detect forging sender addresses during the delivery of the email. https://en.wikipedia.org/wiki/Sender_Policy_Framework
DKIM - DomainKeys Identified Mail - an email authentication method designed to detect forged sender addresses in emails (email spoofing), a technique often used in phishing and email spam. https://en.wikipedia.org/wiki/DomainKeys_Identified_Mail
DMARC - Domain-based Message Authentication, Reporting and Conformance - is an email authentication protocol. It is designed to give email domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. https://en.wikipedia.org/wiki/DomainKeys_Identified_Mail
 TDS is incorporating the protection listed above into the Private Email domains we host for our clients.
TDS is incorporating the protection listed above into the Private Email domains we host for our clients.
Stay Engaged
While we will always continue to enhance protection with technological advancements, all the best cybersecurity products in the world cannot replace an informed and engaged user.
Stay engaged with your technology, cybersecurity products, our resources, and our people to maximize your security and process of digital transformation. Please contact us if you have any questions.
Thanks for reading,

Brad Deflin
Click to view in browser