July Letter
Three for the '20s.
Hi there,
Today marks 2020's mid-point. Looking at current conditions and thinking about the past six months, it's hard to conceive the range of possibilities for the rest of the year.
It is the pace, degree, and nature of change that makes 2020 a historically important and challenging time. Regardless of political views and individual opinions of the year's events, the constant for all is personal security and safety are increasingly at risk from new fronts that are here to stay.
Periods of significant change make it difficult to think clearly and strategically because everything feels like a moving target. Where does one focus? How do you decide what actions help manage the changes and make the most difference for the near and long-term?
For July's letter, and as a risk manager and cybersecurity expert, I'll use Kierkegaard's famous quote as a lens to focus and offer "Three Strategies for Personal Risk Management in the 2020s."
“Life can only be understood backwards; but it must be lived forwards.”
Søren Kierkegaard
Three Strategies for Personal Risk Management in the 2020s
The last couple of weeks closed the case on what 2020 has been trying to tell us all along; expect to need and use PPE soon, if not already. When adding my understanding of viruses and humans and applying Kierkegaard's wisdom to "live forward," I think it's smart to equip oneself to make intelligent decisions about PPE in 2020 and beyond.
Strategy #1 - Get a Face Mask You Can Live With
I find face masks terribly uncomfortable. I can't breathe, they muffle speech, and all I can smell is my breath. I've tried different disposable versions, but couldn't tolerate any for more than five or ten minutes before I wanted to tear it off.
So, I searched the internet for a better solution. After a few makes and models, I found Envo and took a shot by ordering a couple of their N95 masks.
About three weeks after my order, the masks arrived. Each one includes five N95 replacement filters and a carrying case. I figured out the best way to put it on is with the lanyard first, then the ear-hooks. Pulling the string just snug enough makes the gel liner seal the face and sort of hang on the bridge of the nose. The effect is comfortable, and the mask stays put without pulling on the ears.
To take it off, I unhook the ear clips and let it fall from the lanyard to either hang or remove altogether. The procedure is comfortable and straightforward, and after some practice, I can take it on or off with one hand.
I'm two weeks in with the Envo and can report - this is a great mask! For me, it's a considerable improvement in comfort and convenience. It doesn't smash down my nose or fog my sunglasses near as much as other models. I clean the plastic and gel parts with soap and water and keep it in its case, so its ready when I need it.
 The Envo N95 Gel Mask
The Envo N95 Gel Mask
The Envo mask isn't perfect, but it's a big step in the right direction for PPE. And it isn't cheap, but I see it as a tool for change. Here's why:
The process of finding a mask I could live with forced me to think critically about my PPE. What are my options, and how do I evaluate them? What should I expect in terms of availability and pricing? What can I do to avoid buying my PPE reactively with the masses and not getting what I want?
Hopefully, the mask goes under-used. But as things change if I have to think critically about PPE, I'm prepared to act intelligently.
 For 2020 and beyond, own a mask you can live with.
For 2020 and beyond, own a mask you can live with.
Strategy #2 - Learn Password Management
Seriously, it's time, and my best advice right now includes learning to manage your passwords. Let's use Kierkegaard's logic again and look back to live forward.
Bad password habits are always a top reason for successful hacks. And 2020 tells us the next decade includes more internet activity across all aspects of life, an increasing number of online accounts, and an increase in sensitivity and vulnerability of personal information. Using good passwords and managing them lops off a huge piece of your overall risk to privacy, security, and overall safety.
Yes, Face ID and other authentication methods will be increasingly available to reduce login hassles. But for me, a password manager acts as a convenient and well-organized repository of sensitive information, credentials, and identification - not just for logging in. Learning to store confidential information in a highly secure way while keeping it conveniently accessible and retrievable, across all devices and accounts, is a life-skill that will serve well in the 2020s.
What makes a secure password? Using math as leverage against brute-force password hacking takes a minimum of 14 characters. Our brains are not wired to store 14 character strings, so it takes technique and tools to do it without frustration, inconvenience, and loss.
Commit just 30 to 60 minutes of undivided attention to learn how to make a great password and use a password manager app.
How to Make Great Passwords
Yes, Password Managers are Safe
Password Meter
I use LastPass. Some prefer 1Password, and it is an excellent tool as well.
 Use a password manager to securely and conveniently store, manage, and retrieve sensitive personal information.
Use a password manager to securely and conveniently store, manage, and retrieve sensitive personal information.
Strategy #3 - Seek Digital Autonomy
Personal information has been called the "new oil" by some because it's a commodity with high intrinsic value. Yet, in the U.S., we voluntarily give it away for free. Many don't know or care that the personal information we don't give away "voluntarily" is taken or stolen in the most surreptitious ways only to be used against us eventually.
Using the Kierkegaard rearview mirror, and understanding the damage done by the unabated abuse of personal information, it's smart to live forwards by seeking some autonomy from the chief abusers.
 For personal risk management in the 2020s, seek digital autonomy from Big Tech, Big Government, and Big Business.
For personal risk management in the 2020s, seek digital autonomy from Big Tech, Big Government, and Big Business.
Here are three things that will substantially increase digital autonomy for reclaiming privacy and control of your personal information:
- Privatize Your Email Account
When Big Tech, Big Government, and Big Business want to flex big muscle, knowing your email activity and controlling what does and doesn't get to your inbox is a significant lever. The term is "Filter Bubble," and I wrote about it here.
Big-everything is mining personal email in "free" accounts, and it will get increasingly worse with more severe potential consequences. Privatizing lifts your email off this grid of abuse and will provide a trusted communication channel for life, including future generations for some.
With a privately owned email domain, your information is yours, your inbox is safe, there are no ads, and no third-party algorithms will determine what gets to your inbox.
 Privatize your email for reclaiming privacy and ownership of personal information.
Privatize your email for reclaiming privacy and ownership of personal information.
- Use a VPN Everyday
A VPN uses encryption to make your online activities anonymous and invisible to the outside, including over public Wi-Fi. And, importantly, it brings the power of encryption into your everyday life.
Encryption-based tools are evolving, and before long, they will be used to solve privacy and security concerns across many of our daily activities.
 Use a VPN app for online anonymity and to prepare for other encryption-based solutions as they become available in the 2020s.
Use a VPN app for online anonymity and to prepare for other encryption-based solutions as they become available in the 2020s.
- Install a Private Internet Network and WiFi at Home
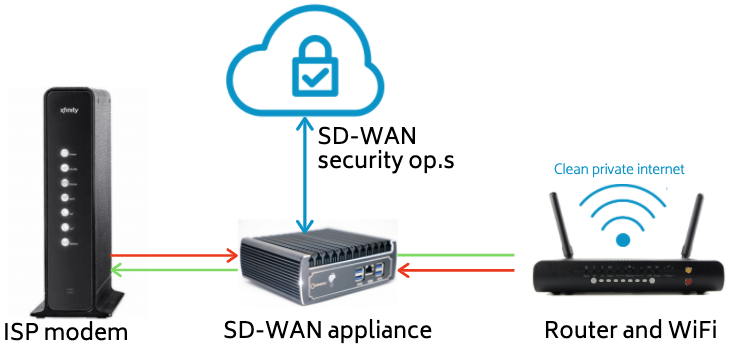
Innovation in enterprise-grade network security is on fire, and TDS equips clients with an advanced SD-WAN system to protect their homes and home offices with private internet and WiFi.
The effect is a "clean" and private network that protects the bad from getting in and anonymizes all information and communications before it goes out to the internet.
This is a simple diagram but illustrates how an SD-WAN system delivers comprehensive cybersecurity across your network and all its internet-connected devices and appliances.
For a deeper dive to SD-WAN and the future of privacy and cybersecurity technology, here are some industry reports by leading providers, research firms, and data scientists:
Network World 2020 - State of the Network: SD-WAN
Guide to Secure SD-WAN
CB Insights on Enterprise SD-WAN (SDN)
 Use SD-WAN technology to avoid all internet-related risks and protect all home and home office digital activities.
Use SD-WAN technology to avoid all internet-related risks and protect all home and home office digital activities.
Taking what we know about the state of personal information today and living forward for the 2020s, digital autonomy is increasingly about privacy, security, personal safety, individual rights, and freedom.
Getting Started with Living Forward for the 2020s
This might seem like a lot, but it's manageable. It's vital to see adaptation to change as a process and to take things step by step. We're here to help - we've been providing enterprise-grade privacy and cybersecurity systems to individuals and families since 2013. You can contact me or Diane Kisner at any time for more information and a consultation.
For now, we wish you and your family a safe and healthy July 4th.
Thanks for reading,

Brad Deflin
Click to view in browser
