January Letter
Hi there,
When running into old friends and associates, they sometimes say, "Tell me what you do again." It's not that they forgot I'm in the cybersecurity business, but less clear is what that means, and for whom.
So, we made "About Total Digital Security," and it's linked in the top tile below.
Cybersecurity = great tech + informed individual
Successful cybersecurity is half about technology and half about people. You cannot have success with one in the absence of the other. The ambient nature of digital risk requires consistent and reliable protection from technology, coupled with an informed and aware user. It doesn't work otherwise, which is the driving reason cyber has become humanity's greatest challenge today (W.Buffet.)
We coined "Cybersecurity for Life" because digitally powered machines and networks are changing everything relating to daily life - personally and professionally. And it's happening at a pace foreign and unnatural to humans. The effect is putting the notion of risk on its head as most are unaware and unprepared.
Which brings us back to "What do you do again?"
Well, when you equip an engaged user with new, highly effective cyber defenses, the risk is reduced to the thinnest of margins. So, our mission is to bring individuals and solutions together. We do it by using the internet to make best-in-class solutions accessible, affordable, and simple to use. And we continually inform and educate our clients with threat updates, best practices, and our distinct observations and insights from the field. Our clients are not only protected, but developing life-skills that will serve for a lifetime.
Cybersecurity for Life - it's not only just what we do but our mission, and we're committed to the cause of helping others find the privacy, security, safety, and autonomy they seek in the new digital age.
Cybersecurity Simplified
In June last year, I presented to Montana's 9th Judicial District on "Cybersecurity Simplified." My goal was to explain the democratization of cyber risk and the corresponding fountain of innovation in IT security.
A transcript of the presentation with accompanying charts and graphs includes:
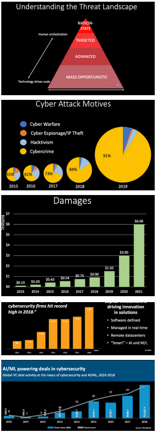 - Understanding Cyber Risk- Attack Motives- Attack Targets- Attack Damages- The New Generation of Perpetrators- Mitigating Cyber Risk- Advancement in IT Security Tech- Using Solutions to Protect- The Human Factor
- Understanding Cyber Risk- Attack Motives- Attack Targets- Attack Damages- The New Generation of Perpetrators- Mitigating Cyber Risk- Advancement in IT Security Tech- Using Solutions to Protect- The Human Factor
Click for more: https://www.totaldigitalsecurity.com/blog/cyber-risk-mitigation-law-cle
Thanks for reading,

Brad Deflin
Click to view online
Click to print from PDF