August Letter
Three A's for August
Hi there,
The dog days of August 2020 start fittingly enough with a hurricane named Isais, which in Spanish means "God Is My Salvation." In turn, salvation means "preservation or deliverance from harm, ruin, or loss."
The CyberAdvisor newsletter is all about preserving from harm, ruin, and loss with preemptive risk management measures that safeguard privacy and increase personal safety.
In this month's letter, we sum it up with the "Three A's for August."
- Authenticate what comes in
- Anonymize what goes out
- Autonomy from Big Tech's manipulation and abuse matters
1. Authenticate First
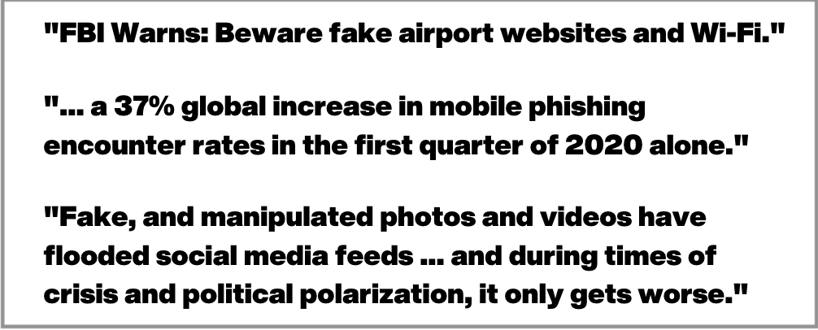
In the digital age, trust nothing on face value.
Email, websites, WiFi networks, photos, and the 'news'- in many cases, are fake and engineered to manipulate our thoughts and actions.
 Authentication means thinking critically about identifying and credentialing your interaction with the internet and media.
Authentication means thinking critically about identifying and credentialing your interaction with the internet and media.
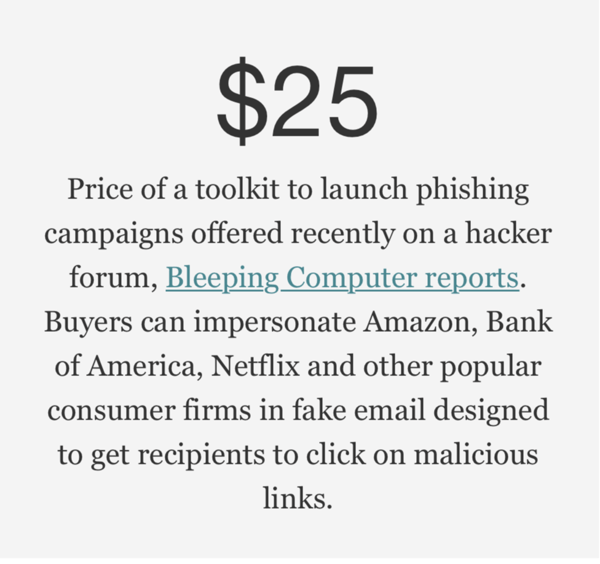
Avoid being "spoofed" by making a habit of first asking:
- Who is really sending me this email?
- Is this website what it purports to be?
- Is that headline meant to inform or influence?
- Do I trust the WiFi I'm using?
Learn to authenticate all your primary digital feeds, and with a nod to Ronald Reagan: Verify before trusting!
 Note - all Private Email domains for our clients include DKIM authentication built-in for every box.
Note - all Private Email domains for our clients include DKIM authentication built-in for every box.
2. Anonymize Your Internet Activities
Encryption is like a silver bullet for privacy and information security because it anonymizes digital activity. This explains certain governments outlawing the possession and use of a VPN. 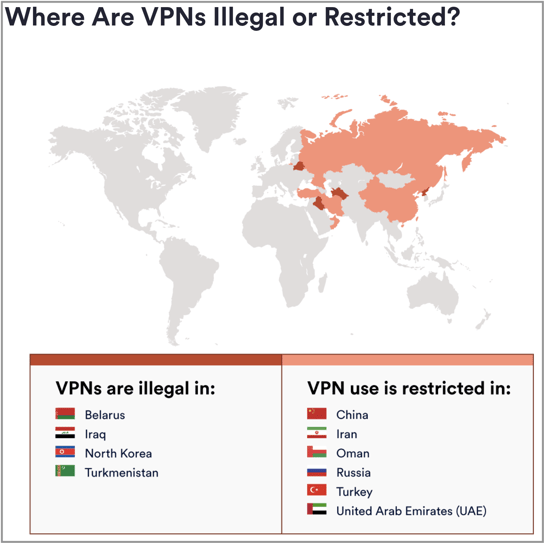 Fortunately, encryption tools are getting better and easier to use. We suggest using a VPN to beginning immediately reducing your digital footprint and to increasingly learn how to use encryption to increase privacy and control your personal information.
Fortunately, encryption tools are getting better and easier to use. We suggest using a VPN to beginning immediately reducing your digital footprint and to increasingly learn how to use encryption to increase privacy and control your personal information.
 We suggest embracing encryption as much as you can in all digital activities by anonymizing internet activity and email across your home networks and personal devices.
We suggest embracing encryption as much as you can in all digital activities by anonymizing internet activity and email across your home networks and personal devices.
3. Autonomy from Big Tech Matters
Are you watching what Big Tech is doing as a standard operating practice to feed their business models? Our American democracy has been hacked, and it's time to defund Big Tech and social media.

To the mega-billionaire owners of the ruling information industrial complex, you are but a dollar sign at the bottom of their chain. To resist information dysfunction, seek more digital autonomy starting now.
 Digital autonomy begins with privatizing email and positioning your most vital communication and social channel off the grid of Big Tech's control and abuse.
Digital autonomy begins with privatizing email and positioning your most vital communication and social channel off the grid of Big Tech's control and abuse.
Contact me to start taking control of your digital self and personal information and position for survival and success in the digital age.
Thanks for reading,

Brad Deflin
Click to view in browser